I got Wordpress installed on a Windows Server following the instruction in the post: Installing Wordpress on Windows.
My Wordpress site is on a Virtual Machine while the database server is on a physical machine connected via a private LAN. Since the mySQL database server is one another machine, I have to choose Remote Database option for the installation.
The installation when fine but when I access the site, I got an error message saying it couldn't login to the database. I checked the database and I can see the database has been created and the user has permission but the thing is, the user permission wasn't properly setup. The scope has been limited to "localhost" and as the result the connection from the VM got denied.
Easy fix, I thought. I proceed to change the scope to the grant access from remote machine. But that didn't help either. My next action was to check the database itself and I can see that it has already been created. Looking into the tables, I see none. So apparently, during the installation, the root password was asked but the installer did not use it to create tables and instead, the wordpress user account is used to create them instead and since remote connection wasn't allowed, it couldn't login to create the table so the database is empty.
Bottom line is changing the scope to allow for remote connection on the wordpressuser account don't work. I tried creating the user before the installation, but that didn't work either since a new one with the same scope showed up and ruin the party.
So I decided to use the root account/password to install it instead of creating a new user and things went well. My site was up and running in less than 30 seconds. But now my site is running with the root password which didn't sound good.
Poking around in the wordpress folder, I found a file called wp-config.php. This file contains the database settings among other things. I locate the database user, get rid of the root user and replace it with the one I created for the site.
Now I got Wordpress running on a less privileged account. If you are having issue installing Wordpress on Windows using a remote database server, I hope this blog helps you.
Showing posts with label Windows. Show all posts
Showing posts with label Windows. Show all posts
Friday, May 11, 2012
Installing Wordpress on Windows
So I decided to use Wordpress as the blogging platform and since I am more comfortable getting around in Windows environment, I decided to install Wordpress on Windows. There are a few ways to get it installed on Windows but the quickest and easiest way (or so they say) is to use the Microsoft Web Platform Installer.
Just follow these steps:
That should be it. You should have a wordpress site running on a Windows server now unless you are like me... using a another server for database storage run into some other errors.
If you do run into an issue using remote database server then check out this post: Installing Wordpress on Windows Using Remote Database Server.
Just follow these steps:
- Launch Microsoft Web Platform Installer
- Click on Applications (at the top)
- Click Add button on the Wordpress item
- Finally, click Install button at the bottom of the screen
That should be it. You should have a wordpress site running on a Windows server now unless you are like me... using a another server for database storage run into some other errors.
If you do run into an issue using remote database server then check out this post: Installing Wordpress on Windows Using Remote Database Server.
Sunday, February 28, 2010
Earlier this week, I released a suite of Windows network troubleshooting utilities called Pinkie through a website named ipUptime.net.
Everything went well. The public seems to welcome it and as I monitor the statistics for the site as well as the download counts from other download sites, I realized that something is wrong with my site statistics; the numbers don't match up and my number came up short.
As I found out, if people download the Pinkie through the link on my site then the download count is incremented. But if they had download it from other sites, using the URL I had published then the download is not accounted for.
Changing the published URL for all other sites will be time consuming so I was looking for a better solution to the issue. Then I remember ASP.net 2.0 supports URL Mappings. So by using URL Mappings, within a minute or two, my problem is solved.
Here's the syntax for URL Mappings:
<urlmappings>
<add url="~/newurl.aspx" mappedurl="~/oldURL.aspx"></add>
</urlmappings>
Best use for URL Mappings are for shortening long, hard to remember URL to something short & easy to remember or in my case, correct a mistake and save time.
Everything went well. The public seems to welcome it and as I monitor the statistics for the site as well as the download counts from other download sites, I realized that something is wrong with my site statistics; the numbers don't match up and my number came up short.
As I found out, if people download the Pinkie through the link on my site then the download count is incremented. But if they had download it from other sites, using the URL I had published then the download is not accounted for.
Changing the published URL for all other sites will be time consuming so I was looking for a better solution to the issue. Then I remember ASP.net 2.0 supports URL Mappings. So by using URL Mappings, within a minute or two, my problem is solved.
Here's the syntax for URL Mappings:
<urlmappings>
<add url="~/newurl.aspx" mappedurl="~/oldURL.aspx"></add>
</urlmappings>
Best use for URL Mappings are for shortening long, hard to remember URL to something short & easy to remember or in my case, correct a mistake and save time.
Monday, April 21, 2008
Virtual Private Networks Troubleshooting - Part I
I've seen quite a number of posts asking why VPN users are not able to access their network even though they have been successfully connected.
Let's try to troubleshoot what happens here. A very common VPN setup is to use 2 NICs and run Routing and Remote Access on one of them. The benefits of this would be that you can isolate VPN traffic and keeping it from overloading the NIC that handles the internal network traffic. One thing to note for is that the two NICs have to be assigned IPs from different networks or subnets. For example:
1st NIC (VPN): 192.168.1.2 /24
2nd NIC(internal network): 192.168.2.2 /24
(Don't worry if you don't understand the /24. It's called the slash notation for the subnet mask which is the equivalent of 255.255.255.0)
Through the initial RRAS setup, users will be able to connect to the VPN just fine and will be assigned an IP address of one of the networks. The problem arise when they try to connect to network resources on through the 2nd NIC (the other network). This is due to the fact that Windows doesn't know how to route the packets from the 192.168.1.0 network to 192.168.2.0 network.
You can tell Windows how to route traffic between the two NICs by configuring a static route with the "Route" command. Type "Route /?" at the Command Prompt for more information.
And as usual, I have a second way to accomplish the job by turning on Routing using RIP or OSPF and add the two NICs to it.
One thing that I see lacking from most Windows Administrators is the understanding of TCP/IP and network routing. I would recommend Windows Administrators to take CCNA anytime. Even though it might seem so remote from their daily tasks, one can walk away from a CCNA class with so much helpful information that makes their job much easier to do.
Let's try to troubleshoot what happens here. A very common VPN setup is to use 2 NICs and run Routing and Remote Access on one of them. The benefits of this would be that you can isolate VPN traffic and keeping it from overloading the NIC that handles the internal network traffic. One thing to note for is that the two NICs have to be assigned IPs from different networks or subnets. For example:
1st NIC (VPN): 192.168.1.2 /24
2nd NIC(internal network): 192.168.2.2 /24
(Don't worry if you don't understand the /24. It's called the slash notation for the subnet mask which is the equivalent of 255.255.255.0)
Through the initial RRAS setup, users will be able to connect to the VPN just fine and will be assigned an IP address of one of the networks. The problem arise when they try to connect to network resources on through the 2nd NIC (the other network). This is due to the fact that Windows doesn't know how to route the packets from the 192.168.1.0 network to 192.168.2.0 network.
You can tell Windows how to route traffic between the two NICs by configuring a static route with the "Route" command. Type "Route /?" at the Command Prompt for more information.
And as usual, I have a second way to accomplish the job by turning on Routing using RIP or OSPF and add the two NICs to it.
One thing that I see lacking from most Windows Administrators is the understanding of TCP/IP and network routing. I would recommend Windows Administrators to take CCNA anytime. Even though it might seem so remote from their daily tasks, one can walk away from a CCNA class with so much helpful information that makes their job much easier to do.
Tuesday, January 1, 2008
Changing Computer SID
I've been working on a SharePoint project that requires a domain controller, an IIS web farm and a SQL Server. In order to quickly setup my development environment, I use Virtual Server 2005 and created a number of virtual machines and set them up in an isolated virtual network.
I started out by setting up a barebone Windows Server 2003 with SP2 and .Net Framework 2.0. After all the security updates have been applied, I copied the virtual hard drive (.vhd) file, renaming it and attached to the new virtual machines. I brought them up one by one and renamed them. Once I got through all four, they all came up with no problem.
When I promoted the DC and start joining the first member server things also went pretty well until I tried to logon to the member server with a domain account. The error message I received was:
The name or security ID (SID) of the domain specified is inconsistent with the trust information for that domain
This error occurred because I used only one installation of Windows 2003 Server. The SID is the same on all of my virtual machines because I just simply copied the .vhd file and renamed it.
The solution was to download NewSID utility from SysInterals (now owned by Microsoft). The tool allows you to change SID as well as computer name and works wonderfully in this situation.
Here's a few tips for those who might run into this same scenario:
1. Run NewSID when you bring up a clone server/computer and let it do the rename for you. This will save you from rename the computer, reboot, login then change the SID only to reboot again.
2. Run NewSID before you join the member server to the domain. This is because it will save you from all the hassle of joining domain, reboot, unjoin, reboot, change SID reboot and rejoin domain...
I started out by setting up a barebone Windows Server 2003 with SP2 and .Net Framework 2.0. After all the security updates have been applied, I copied the virtual hard drive (.vhd) file, renaming it and attached to the new virtual machines. I brought them up one by one and renamed them. Once I got through all four, they all came up with no problem.
When I promoted the DC and start joining the first member server things also went pretty well until I tried to logon to the member server with a domain account. The error message I received was:
The name or security ID (SID) of the domain specified is inconsistent with the trust information for that domain
This error occurred because I used only one installation of Windows 2003 Server. The SID is the same on all of my virtual machines because I just simply copied the .vhd file and renamed it.
The solution was to download NewSID utility from SysInterals (now owned by Microsoft). The tool allows you to change SID as well as computer name and works wonderfully in this situation.
Here's a few tips for those who might run into this same scenario:
1. Run NewSID when you bring up a clone server/computer and let it do the rename for you. This will save you from rename the computer, reboot, login then change the SID only to reboot again.
2. Run NewSID before you join the member server to the domain. This is because it will save you from all the hassle of joining domain, reboot, unjoin, reboot, change SID reboot and rejoin domain...
Thursday, December 27, 2007
ICMP - Pinging Server 2008
One of the most common ways for an administrator to see if a particular server is up or not is to send an ICMP package to the server or to Ping it. This is also called an Echo Request.
Windows Server 2008 disable this Echo Request by default. Here's how you can turn this on:
1. Open Server Manager
2. Expand Configuration section
3. Expand Windows Firewall with Advanced Security (OK, Microsoft, is there a Basic one???)
4. Click on Inbound Rules
5. In the middle pane, scroll down and find "File and Printer Sharing (Echo Request - ICMPvX-in)" where the X stands for the IP version number
6. Right click it and select Enable
7. If you want to edit advanced options then right click it and select Properties option instead
If you are running the core version, you can accomplish the same thing by issuing the netsh command:
netsh firewall set icmpsetting 8
Windows Server 2008 disable this Echo Request by default. Here's how you can turn this on:
1. Open Server Manager
2. Expand Configuration section
3. Expand Windows Firewall with Advanced Security (OK, Microsoft, is there a Basic one???)
4. Click on Inbound Rules
5. In the middle pane, scroll down and find "File and Printer Sharing (Echo Request - ICMPvX-in)" where the X stands for the IP version number
6. Right click it and select Enable
7. If you want to edit advanced options then right click it and select Properties option instead
If you are running the core version, you can accomplish the same thing by issuing the netsh command:
netsh firewall set icmpsetting 8
IIS 7 - FTP Server
I was evaluating the much anticipated Windows Server 2008 RC1 and one of the areas I was focusing on was IIS7. Pretty much every component was updated except for the FTP server. It seems that Microsoft was rushing RC1 out and didn't have enough time to add the new FTP server in there so they went with the old version instead.
When you enable FTP role, the old IIS 6 snapin will be added to let you manage the FTP server. I didn't like the way it turned out and searched around a bit more and found out FTP Server 7 RC0 is out.
You can download the new FTP Server here. In order to install this package, you must first uninstall the old FTP version.
When you enable FTP role, the old IIS 6 snapin will be added to let you manage the FTP server. I didn't like the way it turned out and searched around a bit more and found out FTP Server 7 RC0 is out.
You can download the new FTP Server here. In order to install this package, you must first uninstall the old FTP version.
Sunday, December 16, 2007
Windows 2008 Hyper-V Installation - Login
I was checking out Windows 2008 Hyper-V RC1. Downloaded the ISO image and installed it. Everything went pretty well with minimum user intervention. After a couple of auto reboots the login window appeared and I had only one option - Other Login (for the core installation).
I was scratching my head trying to figure out what login I can use since the installation didn't ask me to create any login. So I tried out a couple of well known default username and password and finally I got in with the Administrator & blank password combination.
Once I logged in, I was presented with the good old Command prompt. For those of you who are used to the Windows interface, this might be a bit of a shocker.
The next thing I did was to enable Hyper-V in the core server deployment. This was done with the command:
Start /w ocsetup Microsoft-Hyper-V
A reboot is required once Hyper-V is enabled. Please note that the command is case sensitive so you must type the command exactly as seen here.
I was scratching my head trying to figure out what login I can use since the installation didn't ask me to create any login. So I tried out a couple of well known default username and password and finally I got in with the Administrator & blank password combination.
Once I logged in, I was presented with the good old Command prompt. For those of you who are used to the Windows interface, this might be a bit of a shocker.
The next thing I did was to enable Hyper-V in the core server deployment. This was done with the command:
Start /w ocsetup Microsoft-Hyper-V
A reboot is required once Hyper-V is enabled. Please note that the command is case sensitive so you must type the command exactly as seen here.
Tuesday, December 11, 2007
How to set up SQL Server to listen on multiple static TCP ports
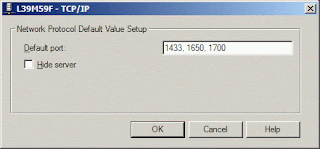
Did you know you can have your MS SQL Server listen on multiple TCP ports? I find this feature very useful since I run my DB server on a specific port and often run into clients that require to have database connection on a different port because it falls inline with their security practice.
Here's how you can do it:
1. Start SQL Server Network Utility
2. Select TCP/IP and click Properties button
3. Enter the port numbers (separated by commas)
4. Click OK twice
5. Stop & restart SQL Server for the change to take effect
Tuesday, December 4, 2007
Terminal Services Client (MSTSC) and Vista/2008
A few months back, I wrote a blog about as you can see here.
Well, in the newer version of MSTSC for Windows Vista and Windows 2008, the "/console" option is no longer available. However, you can use a new switch "/admin".
This new switch has an advantage that "/admin" session can still be created when the session count has maxed out. Also, the "/admin" sessions don't count toward the session limit that may be configured on a terminal server to limit the number of sessions.
Well, in the newer version of MSTSC for Windows Vista and Windows 2008, the "/console" option is no longer available. However, you can use a new switch "/admin".
This new switch has an advantage that "/admin" session can still be created when the session count has maxed out. Also, the "/admin" sessions don't count toward the session limit that may be configured on a terminal server to limit the number of sessions.
Monday, October 15, 2007
Using Enumerations To Document Your Code
Enumeration is a great way to assign easy to understand & remember textual names to your values. Consider the example:
Public Sub CityWork(ByVal CityID As Integer)
If CityID = 0 Then
'do something
ElseIf CityID = 1 Then
'do something
ElseIf CityID = 2 Then
'do something
Else
'do something
End If
End Sub
By the look of that, the code is pretty hard to understand as you have to remember what all those numbers are to associate with their function. To clarify things a bit, we can modify the above code using enumeration:
Public Enum CityTypes
SanDiego
SanFrancisco
SanJose
End Enum
Public Sub CityWork(ByVal CityID As CityTypes)
If CityID = CityTypes.SanDiego Then
'do something
ElseIf CityID = CityTypes.SanFrancisco Then
'do something
ElseIf CityID = CityTypes.SanJose Then
'do something
Else
'do something
End If
End Sub
Now this code is pretty much self-documented. It makes it so much easier to understand and will also allows you to take advantage of intellisense to help you code faster.
By default, the first enumerated value (SanDiego in this case) will have a value of 0. You can change that by explicitly assign an integer to it. The next enumerated value, if not specified, will be increased by 1 from the previous value (SanJose = 6)
Public Enum CityTypes
SanDiego = 1
SanFrancisco = 5
SanJose
End Enum
If you write your code this way, you'll find that it's much easier to understand, you can code faster, it's less prone to errors and at the same time, you pretty much self-documented the code.
Public Sub CityWork(ByVal CityID As Integer)
If CityID = 0 Then
'do something
ElseIf CityID = 1 Then
'do something
ElseIf CityID = 2 Then
'do something
Else
'do something
End If
End Sub
By the look of that, the code is pretty hard to understand as you have to remember what all those numbers are to associate with their function. To clarify things a bit, we can modify the above code using enumeration:
Public Enum CityTypes
SanDiego
SanFrancisco
SanJose
End Enum
Public Sub CityWork(ByVal CityID As CityTypes)
If CityID = CityTypes.SanDiego Then
'do something
ElseIf CityID = CityTypes.SanFrancisco Then
'do something
ElseIf CityID = CityTypes.SanJose Then
'do something
Else
'do something
End If
End Sub
Now this code is pretty much self-documented. It makes it so much easier to understand and will also allows you to take advantage of intellisense to help you code faster.
By default, the first enumerated value (SanDiego in this case) will have a value of 0. You can change that by explicitly assign an integer to it. The next enumerated value, if not specified, will be increased by 1 from the previous value (SanJose = 6)
Public Enum CityTypes
SanDiego = 1
SanFrancisco = 5
SanJose
End Enum
If you write your code this way, you'll find that it's much easier to understand, you can code faster, it's less prone to errors and at the same time, you pretty much self-documented the code.
Monday, October 1, 2007
How To Truncate Log File In SQL Server 2005
I as part of my development role, often perform database backup/restore operations and move the databases from one server to another (ie: development to test, to QA...). One issue I often encounter is the amount of data I have to transfer from one server to another. If the server is on a local network then it's not a big deal but if it goes out to a remote data center then I want to cut the file size down as much as I can.
I accomplished by eliminating the log file thus trim down a nice portion of unnecessary data. Here are the steps:
1. Take the database offline
2. Detach the database
3. Delete or rename the log file
4. Attach the database without the log file (highlight the log file and click Remove button)
SQL Server should create a new log file for your database. At this time, I backup the database and send it to the new server. I find this process has helped me save a quite a bit of time, especially when setting up the database on a remote server.
I accomplished by eliminating the log file thus trim down a nice portion of unnecessary data. Here are the steps:
1. Take the database offline
2. Detach the database
3. Delete or rename the log file
4. Attach the database without the log file (highlight the log file and click Remove button)
SQL Server should create a new log file for your database. At this time, I backup the database and send it to the new server. I find this process has helped me save a quite a bit of time, especially when setting up the database on a remote server.
Thursday, August 30, 2007
Disable Windows Error Reporting
Every now and then I run into one of these application or system error that pops up the Error Reporting dialog box. This is one way Microsoft is getting the feedback from users on how well (or not) their software is performing or interacting with other applications and improve their products.
This is fine with me but sometimes, it gets really annoying when the same error keeps occurring and you have to report, wait and then close the dialog box or choose not to report it. To get rid of this headache once and for all, you can turn off this feature completely.
1. Launch System Properties dialog box
2. Click on Advanced Tab
3. Click on Error Reporting button
4. Select "Disable error reporting" radio button
5. Click OK twice to exit
You can launch System Properties dialog box through the Control Panel or by Right Click on My Computer then select Properties. Another way to bring it up is to press the [Windows][Break] key combinations.
This is fine with me but sometimes, it gets really annoying when the same error keeps occurring and you have to report, wait and then close the dialog box or choose not to report it. To get rid of this headache once and for all, you can turn off this feature completely.
1. Launch System Properties dialog box
2. Click on Advanced Tab
3. Click on Error Reporting button
4. Select "Disable error reporting" radio button
5. Click OK twice to exit
You can launch System Properties dialog box through the Control Panel or by Right Click on My Computer then select Properties. Another way to bring it up is to press the [Windows][Break] key combinations.
Monday, August 13, 2007
Web Application Security
Web applications are at great risks due to the fact that most applications are widely available to anyone with internet access. They often get compromised by script exploits.
Most script exploits require the application to accept malicious input and inject it into a page where it will be executed on the server or in the client browser. The potential damage from such an exploit depends on the script that is being executed (taking over a system, install malware, deleting data...)
The primary defense against script exploit is to never trust the information obtained from users. This apply to both incoming and outgoing data from users (data written to and data pulled from database).
There are many things a developer can do to protect application against script exploits. Data input by users should always be validated. Form elements should be HTML-encoded. Dynamic SQL might be flexible but yet it can compromise your data. Consider parameterized query against SQL queries using string concatenation.
In this simple example:
"Select * From Customers where LastName = " & txtLastName.Value
A malicious user who knows a something about database could turn that SQL statement into:
Select * From Customers Where LastName = 'a'; Delete From Customers Where LastName > ''
And when it gets executed, the database is compromised.
It is very important to understand how users and their data interact with your application. That way you can better protect your data, application and users from script exploits.
For more information on how to protect your web application see Basic Security Practices for Web Applications.
Most script exploits require the application to accept malicious input and inject it into a page where it will be executed on the server or in the client browser. The potential damage from such an exploit depends on the script that is being executed (taking over a system, install malware, deleting data...)
The primary defense against script exploit is to never trust the information obtained from users. This apply to both incoming and outgoing data from users (data written to and data pulled from database).
There are many things a developer can do to protect application against script exploits. Data input by users should always be validated. Form elements should be HTML-encoded. Dynamic SQL might be flexible but yet it can compromise your data. Consider parameterized query against SQL queries using string concatenation.
In this simple example:
"Select * From Customers where LastName = " & txtLastName.Value
A malicious user who knows a something about database could turn that SQL statement into:
Select * From Customers Where LastName = 'a'; Delete From Customers Where LastName > ''
And when it gets executed, the database is compromised.
It is very important to understand how users and their data interact with your application. That way you can better protect your data, application and users from script exploits.
For more information on how to protect your web application see Basic Security Practices for Web Applications.
Download File with Visual Basic
My.Computer.Network namespace provides the DownloadFile method which can be used for downloading a remote file to a specific location.
The basic syntax for calling DownloadFile method is to specify the file's location as a string or URI and the location to store the file as seen below:
My.Computer.Network.DownloadFile("http://www.server.com/readme.txt", "c:\docs\readme.txt")
The overloaded methods allow you to specify more advanced parameter like timeout, username & password for protected file. The example below downloads password protected file.
My.Computer.Network.DownloadFile("http://www.server.com/readme.txt", "c:\docs\readme.txt", "myusername", "mypassword")
Note that FTP protocol is used by the DownloadFile method to send information including username & password in plain text. It should not be used to transmit sensitive information.
The basic syntax for calling DownloadFile method is to specify the file's location as a string or URI and the location to store the file as seen below:
My.Computer.Network.DownloadFile("http://www.server.com/readme.txt", "c:\docs\readme.txt")
The overloaded methods allow you to specify more advanced parameter like timeout, username & password for protected file. The example below downloads password protected file.
My.Computer.Network.DownloadFile("http://www.server.com/readme.txt", "c:\docs\readme.txt", "myusername", "mypassword")
Note that FTP protocol is used by the DownloadFile method to send information including username & password in plain text. It should not be used to transmit sensitive information.
Monday, July 16, 2007
Funky Name
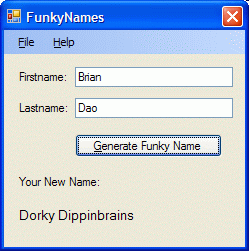 I had a little time to spare and wanted to have some fun to relieve the stress so I created a little application that generate some funky names based on the user's input.
I had a little time to spare and wanted to have some fun to relieve the stress so I created a little application that generate some funky names based on the user's input.The name generation logic is based on a children's book, Captain Underpants And the Perilous Plot Professor Poopypants, by Dave Pilkey, in which the evil Professor forces everyone to assume new names...
The program uses some simple one dimensional arrays and use the user's input to index into the arrays and generate the new name. It also makes use of the one click deployment option.
Pretty funny. Give it a try.
The program can be downloaded from http://www.meshflowers.com/FunkyNames/
Tuesday, July 3, 2007
Reading XML File Using XMLDocument Object
In the previous blog, I discussed how to read XML file using XMLTextReader object of the System.XML namespace. In the same namespace, we also have XMLDocument which can also be used to read XML files.
You can use the Load method to read an XML file and process the elements using XPath selection if you know the structure of the XML document as follow:
Dim myXmlDoc as New XmlDocument
Dim myNode as XmlNode
myXmlDoc.Load("Cars.xml")
myNode = myXmlDoc.SelectSingleNode("/car/honda")
myTextBox.Text = myNode.InnerXml & vbCrLf
The XmlNode object provides the NextSibling method which can be used to move to the next element or node.
myNode = myNode.NextSibling
myTextBox.Text &= myNode.InnerXml
Now that works fine if you know the the structure of the XML document. If you don't know the structure, you can navigate through the document using FirstChild and NextSibling methods.
myNode = myXmlDoc.FirstChild
While myNode.NodeType <> XmlNodeType.Element And Not myNode Is Nothing
myNode = myNode.NextSibling
End While
myTextBox.Text = myNode.InnerXml
 This will dump everything in that node to the textbox including the element names and attributes.
This will dump everything in that node to the textbox including the element names and attributes.
It's not possible to cover all the methods and properties of the XMLDocument and XMLNode in a short blog, but I hope this will get you going.
Further reading should be done on the following topics: XMLDocument, XMLNode, XMLAttribute, FirstChild, HasChildNodes, InnerText, InnerXML...
Download the sample project here.
You can use the Load method to read an XML file and process the elements using XPath selection if you know the structure of the XML document as follow:
Dim myXmlDoc as New XmlDocument
Dim myNode as XmlNode
myXmlDoc.Load("Cars.xml")
myNode = myXmlDoc.SelectSingleNode("/car/honda")
myTextBox.Text = myNode.InnerXml & vbCrLf
The XmlNode object provides the NextSibling method which can be used to move to the next element or node.
myNode = myNode.NextSibling
myTextBox.Text &= myNode.InnerXml
Now that works fine if you know the the structure of the XML document. If you don't know the structure, you can navigate through the document using FirstChild and NextSibling methods.
myNode = myXmlDoc.FirstChild
While myNode.NodeType <> XmlNodeType.Element And Not myNode Is Nothing
myNode = myNode.NextSibling
End While
myTextBox.Text = myNode.InnerXml
 This will dump everything in that node to the textbox including the element names and attributes.
This will dump everything in that node to the textbox including the element names and attributes.It's not possible to cover all the methods and properties of the XMLDocument and XMLNode in a short blog, but I hope this will get you going.
Further reading should be done on the following topics: XMLDocument, XMLNode, XMLAttribute, FirstChild, HasChildNodes, InnerText, InnerXML...
Download the sample project here.
Labels:
System.XML,
VB.net,
Visual Basic.net,
Windows,
xml
Friday, June 29, 2007
Reading XML File Using XMLTextReader
System.XML namespace provides us with the XMLTextReader class which we could use to read and process XML files.
The most commonly used attributes are .Name and .Value which returns information of about the elements and their associated information.
 MoveToNextAttribute method is used to navigate to the next element. The project below uses an OpenFileDialog box to get the XML file which is then passed to XMLTextReader object and open it. Then the Read method is called to read in and processed the entire XML file and put its content into a textbox.
MoveToNextAttribute method is used to navigate to the next element. The project below uses an OpenFileDialog box to get the XML file which is then passed to XMLTextReader object and open it. Then the Read method is called to read in and processed the entire XML file and put its content into a textbox.
In my opinion, reading XML this way is rather confusing. I like reading XML file using XMLDocument object better as it’s very simple and gives you a much clearer view of the whole process.
This sample project can be downloaded here.
The most commonly used attributes are .Name and .Value which returns information of about the elements and their associated information.
 MoveToNextAttribute method is used to navigate to the next element. The project below uses an OpenFileDialog box to get the XML file which is then passed to XMLTextReader object and open it. Then the Read method is called to read in and processed the entire XML file and put its content into a textbox.
MoveToNextAttribute method is used to navigate to the next element. The project below uses an OpenFileDialog box to get the XML file which is then passed to XMLTextReader object and open it. Then the Read method is called to read in and processed the entire XML file and put its content into a textbox.In my opinion, reading XML this way is rather confusing. I like reading XML file using XMLDocument object better as it’s very simple and gives you a much clearer view of the whole process.
This sample project can be downloaded here.
Labels:
System.XML,
VB.net,
Visual Basic.net,
Windows,
xml
Tuesday, June 26, 2007
ListBox - Select Multiple Items
I've seen quite a number of forums posts asking how to get the selected items of a listbox when the listbox selection mode has been changed to allow for multiple items to be selected. It's actually pretty simple to do in .net.
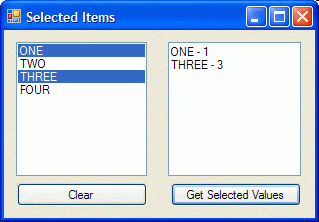 What you need to do is to loop through the SelectedItems collection to get to the items that have been selected. The list box also has a property called SelectedIndices that you can use.
What you need to do is to loop through the SelectedItems collection to get to the items that have been selected. The list box also has a property called SelectedIndices that you can use.
Download the zip file to see the sample code on this which also shows you how to add a name-value pair item like we used to do in VB6.
 What you need to do is to loop through the SelectedItems collection to get to the items that have been selected. The list box also has a property called SelectedIndices that you can use.
What you need to do is to loop through the SelectedItems collection to get to the items that have been selected. The list box also has a property called SelectedIndices that you can use.Download the zip file to see the sample code on this which also shows you how to add a name-value pair item like we used to do in VB6.
Labels:
ComboBox,
Controls,
ListBox,
VB,
VB.net,
Visual Basic,
Visual Basic.net,
Windows
Monday, June 11, 2007
Programmatically Add Event Handlers to Controls At Runtime
If you have read my previous blogs, you'll see that I have discussed about how to add and remove controls at run time. Some controls created at runtime are pretty much useless if they have no event handlers attached to them.
What are event handlers? Think of event handlers as actions that are bound to controls. What action(s) would you want to carry out when certain things happen (ie: like a button is clicked, doubleclicked…)?
Let take a look at the following lines of code:
Dim newButton as Windows.Forms.Button
Dim i As Integer
For i = 1 To 5
newButton = New Windows.Forms.Button
newButton.Name = "btnButton" & i
newButton.Text = "Button " & i
newButton.Top = 20 + i * 30
newButton.Left = 40
Me.Controls.Add(newButton)
Next
The code block above will add 5 buttons to the form at runtime. But when you click on the buttons, nothing happen. Why? This is because at this time, there are no event handlers attached to the buttons.
Let make some modifications:
Public WithEvents newButton As Windows.Forms.Button
Private Sub Form1_Load(ByVal sender As Object, ByVal e As System.EventArgs) Handles Me.Load
Dim i As Integer
For i = 1 To 5
newButton = New Windows.Forms.Button
newButton.Name = "btnButton" & i
newButton.Text = "Button " & i
newButton.Top = 20 + i * 30
newButton.Left = 40
AddHandler newButton.Click, AddressOf ButtonClicked
Me.Controls.Add(newButton)
Next
End Sub
Private Sub ButtonClicked(ByVal sender As Object, ByVal e As EventArgs)
MsgBox("You clicked: " & sender.name &amp; vbCrLf & "Button name: " & sender.Text)
End Sub
Here the newButton has been redefined as a control with events and the AddHandler call attached the method ButtonClicked to the Click event of the control. Note that the control is declared as a global variable. You can’t declare a control with events as a local variable. The address of ButtonClick method is then bound or attached to newButton’s click event. Any time the button is clicked, ButtonClicked method will run and a message box will be displayed.
As you can see, it's pretty straight forward to add, remove and attached events to controls that are created on the fly. This blog only scratches the surface of these issues. You can further your study from these links:
Delegates and the AddressOf Operator
Events and Event Handlers
Download sample code: EventHandlers.zip
What are event handlers? Think of event handlers as actions that are bound to controls. What action(s) would you want to carry out when certain things happen (ie: like a button is clicked, doubleclicked…)?
Let take a look at the following lines of code:
Dim newButton as Windows.Forms.Button
Dim i As Integer
For i = 1 To 5
newButton = New Windows.Forms.Button
newButton.Name = "btnButton" & i
newButton.Text = "Button " & i
newButton.Top = 20 + i * 30
newButton.Left = 40
Me.Controls.Add(newButton)
Next
The code block above will add 5 buttons to the form at runtime. But when you click on the buttons, nothing happen. Why? This is because at this time, there are no event handlers attached to the buttons.
Let make some modifications:
Public WithEvents newButton As Windows.Forms.Button
Private Sub Form1_Load(ByVal sender As Object, ByVal e As System.EventArgs) Handles Me.Load
Dim i As Integer
For i = 1 To 5
newButton = New Windows.Forms.Button
newButton.Name = "btnButton" & i
newButton.Text = "Button " & i
newButton.Top = 20 + i * 30
newButton.Left = 40
AddHandler newButton.Click, AddressOf ButtonClicked
Me.Controls.Add(newButton)
Next
End Sub
Private Sub ButtonClicked(ByVal sender As Object, ByVal e As EventArgs)
MsgBox("You clicked: " & sender.name &amp; vbCrLf & "Button name: " & sender.Text)
End Sub
Here the newButton has been redefined as a control with events and the AddHandler call attached the method ButtonClicked to the Click event of the control. Note that the control is declared as a global variable. You can’t declare a control with events as a local variable. The address of ButtonClick method is then bound or attached to newButton’s click event. Any time the button is clicked, ButtonClicked method will run and a message box will be displayed.
As you can see, it's pretty straight forward to add, remove and attached events to controls that are created on the fly. This blog only scratches the surface of these issues. You can further your study from these links:
Delegates and the AddressOf Operator
Events and Event Handlers
Download sample code: EventHandlers.zip
Subscribe to:
Posts (Atom)
