I got Wordpress installed on a Windows Server following the instruction in the post: Installing Wordpress on Windows.
My Wordpress site is on a Virtual Machine while the database server is on a physical machine connected via a private LAN. Since the mySQL database server is one another machine, I have to choose Remote Database option for the installation.
The installation when fine but when I access the site, I got an error message saying it couldn't login to the database. I checked the database and I can see the database has been created and the user has permission but the thing is, the user permission wasn't properly setup. The scope has been limited to "localhost" and as the result the connection from the VM got denied.
Easy fix, I thought. I proceed to change the scope to the grant access from remote machine. But that didn't help either. My next action was to check the database itself and I can see that it has already been created. Looking into the tables, I see none. So apparently, during the installation, the root password was asked but the installer did not use it to create tables and instead, the wordpress user account is used to create them instead and since remote connection wasn't allowed, it couldn't login to create the table so the database is empty.
Bottom line is changing the scope to allow for remote connection on the wordpressuser account don't work. I tried creating the user before the installation, but that didn't work either since a new one with the same scope showed up and ruin the party.
So I decided to use the root account/password to install it instead of creating a new user and things went well. My site was up and running in less than 30 seconds. But now my site is running with the root password which didn't sound good.
Poking around in the wordpress folder, I found a file called wp-config.php. This file contains the database settings among other things. I locate the database user, get rid of the root user and replace it with the one I created for the site.
Now I got Wordpress running on a less privileged account. If you are having issue installing Wordpress on Windows using a remote database server, I hope this blog helps you.
Showing posts with label Server. Show all posts
Showing posts with label Server. Show all posts
Friday, May 11, 2012
Monday, April 21, 2008
Virtual Private Networks Troubleshooting - Part I
I've seen quite a number of posts asking why VPN users are not able to access their network even though they have been successfully connected.
Let's try to troubleshoot what happens here. A very common VPN setup is to use 2 NICs and run Routing and Remote Access on one of them. The benefits of this would be that you can isolate VPN traffic and keeping it from overloading the NIC that handles the internal network traffic. One thing to note for is that the two NICs have to be assigned IPs from different networks or subnets. For example:
1st NIC (VPN): 192.168.1.2 /24
2nd NIC(internal network): 192.168.2.2 /24
(Don't worry if you don't understand the /24. It's called the slash notation for the subnet mask which is the equivalent of 255.255.255.0)
Through the initial RRAS setup, users will be able to connect to the VPN just fine and will be assigned an IP address of one of the networks. The problem arise when they try to connect to network resources on through the 2nd NIC (the other network). This is due to the fact that Windows doesn't know how to route the packets from the 192.168.1.0 network to 192.168.2.0 network.
You can tell Windows how to route traffic between the two NICs by configuring a static route with the "Route" command. Type "Route /?" at the Command Prompt for more information.
And as usual, I have a second way to accomplish the job by turning on Routing using RIP or OSPF and add the two NICs to it.
One thing that I see lacking from most Windows Administrators is the understanding of TCP/IP and network routing. I would recommend Windows Administrators to take CCNA anytime. Even though it might seem so remote from their daily tasks, one can walk away from a CCNA class with so much helpful information that makes their job much easier to do.
Let's try to troubleshoot what happens here. A very common VPN setup is to use 2 NICs and run Routing and Remote Access on one of them. The benefits of this would be that you can isolate VPN traffic and keeping it from overloading the NIC that handles the internal network traffic. One thing to note for is that the two NICs have to be assigned IPs from different networks or subnets. For example:
1st NIC (VPN): 192.168.1.2 /24
2nd NIC(internal network): 192.168.2.2 /24
(Don't worry if you don't understand the /24. It's called the slash notation for the subnet mask which is the equivalent of 255.255.255.0)
Through the initial RRAS setup, users will be able to connect to the VPN just fine and will be assigned an IP address of one of the networks. The problem arise when they try to connect to network resources on through the 2nd NIC (the other network). This is due to the fact that Windows doesn't know how to route the packets from the 192.168.1.0 network to 192.168.2.0 network.
You can tell Windows how to route traffic between the two NICs by configuring a static route with the "Route" command. Type "Route /?" at the Command Prompt for more information.
And as usual, I have a second way to accomplish the job by turning on Routing using RIP or OSPF and add the two NICs to it.
One thing that I see lacking from most Windows Administrators is the understanding of TCP/IP and network routing. I would recommend Windows Administrators to take CCNA anytime. Even though it might seem so remote from their daily tasks, one can walk away from a CCNA class with so much helpful information that makes their job much easier to do.
Tuesday, January 1, 2008
Changing Computer SID
I've been working on a SharePoint project that requires a domain controller, an IIS web farm and a SQL Server. In order to quickly setup my development environment, I use Virtual Server 2005 and created a number of virtual machines and set them up in an isolated virtual network.
I started out by setting up a barebone Windows Server 2003 with SP2 and .Net Framework 2.0. After all the security updates have been applied, I copied the virtual hard drive (.vhd) file, renaming it and attached to the new virtual machines. I brought them up one by one and renamed them. Once I got through all four, they all came up with no problem.
When I promoted the DC and start joining the first member server things also went pretty well until I tried to logon to the member server with a domain account. The error message I received was:
The name or security ID (SID) of the domain specified is inconsistent with the trust information for that domain
This error occurred because I used only one installation of Windows 2003 Server. The SID is the same on all of my virtual machines because I just simply copied the .vhd file and renamed it.
The solution was to download NewSID utility from SysInterals (now owned by Microsoft). The tool allows you to change SID as well as computer name and works wonderfully in this situation.
Here's a few tips for those who might run into this same scenario:
1. Run NewSID when you bring up a clone server/computer and let it do the rename for you. This will save you from rename the computer, reboot, login then change the SID only to reboot again.
2. Run NewSID before you join the member server to the domain. This is because it will save you from all the hassle of joining domain, reboot, unjoin, reboot, change SID reboot and rejoin domain...
I started out by setting up a barebone Windows Server 2003 with SP2 and .Net Framework 2.0. After all the security updates have been applied, I copied the virtual hard drive (.vhd) file, renaming it and attached to the new virtual machines. I brought them up one by one and renamed them. Once I got through all four, they all came up with no problem.
When I promoted the DC and start joining the first member server things also went pretty well until I tried to logon to the member server with a domain account. The error message I received was:
The name or security ID (SID) of the domain specified is inconsistent with the trust information for that domain
This error occurred because I used only one installation of Windows 2003 Server. The SID is the same on all of my virtual machines because I just simply copied the .vhd file and renamed it.
The solution was to download NewSID utility from SysInterals (now owned by Microsoft). The tool allows you to change SID as well as computer name and works wonderfully in this situation.
Here's a few tips for those who might run into this same scenario:
1. Run NewSID when you bring up a clone server/computer and let it do the rename for you. This will save you from rename the computer, reboot, login then change the SID only to reboot again.
2. Run NewSID before you join the member server to the domain. This is because it will save you from all the hassle of joining domain, reboot, unjoin, reboot, change SID reboot and rejoin domain...
Thursday, December 27, 2007
ICMP - Pinging Server 2008
One of the most common ways for an administrator to see if a particular server is up or not is to send an ICMP package to the server or to Ping it. This is also called an Echo Request.
Windows Server 2008 disable this Echo Request by default. Here's how you can turn this on:
1. Open Server Manager
2. Expand Configuration section
3. Expand Windows Firewall with Advanced Security (OK, Microsoft, is there a Basic one???)
4. Click on Inbound Rules
5. In the middle pane, scroll down and find "File and Printer Sharing (Echo Request - ICMPvX-in)" where the X stands for the IP version number
6. Right click it and select Enable
7. If you want to edit advanced options then right click it and select Properties option instead
If you are running the core version, you can accomplish the same thing by issuing the netsh command:
netsh firewall set icmpsetting 8
Windows Server 2008 disable this Echo Request by default. Here's how you can turn this on:
1. Open Server Manager
2. Expand Configuration section
3. Expand Windows Firewall with Advanced Security (OK, Microsoft, is there a Basic one???)
4. Click on Inbound Rules
5. In the middle pane, scroll down and find "File and Printer Sharing (Echo Request - ICMPvX-in)" where the X stands for the IP version number
6. Right click it and select Enable
7. If you want to edit advanced options then right click it and select Properties option instead
If you are running the core version, you can accomplish the same thing by issuing the netsh command:
netsh firewall set icmpsetting 8
IIS 7 - FTP Server
I was evaluating the much anticipated Windows Server 2008 RC1 and one of the areas I was focusing on was IIS7. Pretty much every component was updated except for the FTP server. It seems that Microsoft was rushing RC1 out and didn't have enough time to add the new FTP server in there so they went with the old version instead.
When you enable FTP role, the old IIS 6 snapin will be added to let you manage the FTP server. I didn't like the way it turned out and searched around a bit more and found out FTP Server 7 RC0 is out.
You can download the new FTP Server here. In order to install this package, you must first uninstall the old FTP version.
When you enable FTP role, the old IIS 6 snapin will be added to let you manage the FTP server. I didn't like the way it turned out and searched around a bit more and found out FTP Server 7 RC0 is out.
You can download the new FTP Server here. In order to install this package, you must first uninstall the old FTP version.
Sunday, December 16, 2007
Windows 2008 Hyper-V Installation - Login
I was checking out Windows 2008 Hyper-V RC1. Downloaded the ISO image and installed it. Everything went pretty well with minimum user intervention. After a couple of auto reboots the login window appeared and I had only one option - Other Login (for the core installation).
I was scratching my head trying to figure out what login I can use since the installation didn't ask me to create any login. So I tried out a couple of well known default username and password and finally I got in with the Administrator & blank password combination.
Once I logged in, I was presented with the good old Command prompt. For those of you who are used to the Windows interface, this might be a bit of a shocker.
The next thing I did was to enable Hyper-V in the core server deployment. This was done with the command:
Start /w ocsetup Microsoft-Hyper-V
A reboot is required once Hyper-V is enabled. Please note that the command is case sensitive so you must type the command exactly as seen here.
I was scratching my head trying to figure out what login I can use since the installation didn't ask me to create any login. So I tried out a couple of well known default username and password and finally I got in with the Administrator & blank password combination.
Once I logged in, I was presented with the good old Command prompt. For those of you who are used to the Windows interface, this might be a bit of a shocker.
The next thing I did was to enable Hyper-V in the core server deployment. This was done with the command:
Start /w ocsetup Microsoft-Hyper-V
A reboot is required once Hyper-V is enabled. Please note that the command is case sensitive so you must type the command exactly as seen here.
Tuesday, December 11, 2007
How to set up SQL Server to listen on multiple static TCP ports
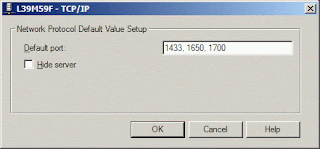
Did you know you can have your MS SQL Server listen on multiple TCP ports? I find this feature very useful since I run my DB server on a specific port and often run into clients that require to have database connection on a different port because it falls inline with their security practice.
Here's how you can do it:
1. Start SQL Server Network Utility
2. Select TCP/IP and click Properties button
3. Enter the port numbers (separated by commas)
4. Click OK twice
5. Stop & restart SQL Server for the change to take effect
Tuesday, December 4, 2007
Terminal Services Client (MSTSC) and Vista/2008
A few months back, I wrote a blog about as you can see here.
Well, in the newer version of MSTSC for Windows Vista and Windows 2008, the "/console" option is no longer available. However, you can use a new switch "/admin".
This new switch has an advantage that "/admin" session can still be created when the session count has maxed out. Also, the "/admin" sessions don't count toward the session limit that may be configured on a terminal server to limit the number of sessions.
Well, in the newer version of MSTSC for Windows Vista and Windows 2008, the "/console" option is no longer available. However, you can use a new switch "/admin".
This new switch has an advantage that "/admin" session can still be created when the session count has maxed out. Also, the "/admin" sessions don't count toward the session limit that may be configured on a terminal server to limit the number of sessions.
Sunday, October 7, 2007
Truncate SQL Logfile
In the last blog, I discussed the process of shrinking the database size to make it easier to move around. The process involved detaching the database and reattaching it. I've an email from one of the readers asking if this can be done while the database is online.
Well, the answer is yes. You can shrink the log file while the database is up. There are two commands that one can use to truncate a log file to reduce its size. They are Backup Log and DBCC ShrinkFile.
Backup Log demo01 with truncate_only
DBCC ShrinkFile('demo01_log', 1)
The commands above will truncate the log file and reduce its size to one megabytes. Before this is carried out though, I highly suggest that you backup your database first.
Well, the answer is yes. You can shrink the log file while the database is up. There are two commands that one can use to truncate a log file to reduce its size. They are Backup Log and DBCC ShrinkFile.
Backup Log demo01 with truncate_only
DBCC ShrinkFile('demo01_log', 1)
The commands above will truncate the log file and reduce its size to one megabytes. Before this is carried out though, I highly suggest that you backup your database first.
Monday, October 1, 2007
How To Truncate Log File In SQL Server 2005
I as part of my development role, often perform database backup/restore operations and move the databases from one server to another (ie: development to test, to QA...). One issue I often encounter is the amount of data I have to transfer from one server to another. If the server is on a local network then it's not a big deal but if it goes out to a remote data center then I want to cut the file size down as much as I can.
I accomplished by eliminating the log file thus trim down a nice portion of unnecessary data. Here are the steps:
1. Take the database offline
2. Detach the database
3. Delete or rename the log file
4. Attach the database without the log file (highlight the log file and click Remove button)
SQL Server should create a new log file for your database. At this time, I backup the database and send it to the new server. I find this process has helped me save a quite a bit of time, especially when setting up the database on a remote server.
I accomplished by eliminating the log file thus trim down a nice portion of unnecessary data. Here are the steps:
1. Take the database offline
2. Detach the database
3. Delete or rename the log file
4. Attach the database without the log file (highlight the log file and click Remove button)
SQL Server should create a new log file for your database. At this time, I backup the database and send it to the new server. I find this process has helped me save a quite a bit of time, especially when setting up the database on a remote server.
Monday, August 13, 2007
Web Application Security
Web applications are at great risks due to the fact that most applications are widely available to anyone with internet access. They often get compromised by script exploits.
Most script exploits require the application to accept malicious input and inject it into a page where it will be executed on the server or in the client browser. The potential damage from such an exploit depends on the script that is being executed (taking over a system, install malware, deleting data...)
The primary defense against script exploit is to never trust the information obtained from users. This apply to both incoming and outgoing data from users (data written to and data pulled from database).
There are many things a developer can do to protect application against script exploits. Data input by users should always be validated. Form elements should be HTML-encoded. Dynamic SQL might be flexible but yet it can compromise your data. Consider parameterized query against SQL queries using string concatenation.
In this simple example:
"Select * From Customers where LastName = " & txtLastName.Value
A malicious user who knows a something about database could turn that SQL statement into:
Select * From Customers Where LastName = 'a'; Delete From Customers Where LastName > ''
And when it gets executed, the database is compromised.
It is very important to understand how users and their data interact with your application. That way you can better protect your data, application and users from script exploits.
For more information on how to protect your web application see Basic Security Practices for Web Applications.
Most script exploits require the application to accept malicious input and inject it into a page where it will be executed on the server or in the client browser. The potential damage from such an exploit depends on the script that is being executed (taking over a system, install malware, deleting data...)
The primary defense against script exploit is to never trust the information obtained from users. This apply to both incoming and outgoing data from users (data written to and data pulled from database).
There are many things a developer can do to protect application against script exploits. Data input by users should always be validated. Form elements should be HTML-encoded. Dynamic SQL might be flexible but yet it can compromise your data. Consider parameterized query against SQL queries using string concatenation.
In this simple example:
"Select * From Customers where LastName = " & txtLastName.Value
A malicious user who knows a something about database could turn that SQL statement into:
Select * From Customers Where LastName = 'a'; Delete From Customers Where LastName > ''
And when it gets executed, the database is compromised.
It is very important to understand how users and their data interact with your application. That way you can better protect your data, application and users from script exploits.
For more information on how to protect your web application see Basic Security Practices for Web Applications.
How To Set Access Key For ASP.net Web Server Controls
Access key combination allows users to press ALT key plus another key to focus or jump to a specific control.
Some controls have Access property where you can set this like TextBox or ListBox. As an alternative, you can set an Access key for a Label control and then tell the browser to associate it with another control. With this approach, you can use the Label control as caption to indicate the access key with an underlined letter.
To set the access key using label control you must:
1. Add the control to be associated
2. Add a Label control
3. Set the access key
4. Associate the control to receive focus
Here's an example:
<asp:Label ID="lblLastName" runat="server"
AccessKey="L"
AssociatedControlID="txtLastName"
Text="<u>L</u>ast name: ">
</asp:Label>
<asp:TextBox ID="txtLastName" runat="server"></asp:TextBox>
Note that setting focus by using access key from a Label control requires that client scripting is enabled in the browser.
Some controls have Access property where you can set this like TextBox or ListBox. As an alternative, you can set an Access key for a Label control and then tell the browser to associate it with another control. With this approach, you can use the Label control as caption to indicate the access key with an underlined letter.
To set the access key using label control you must:
1. Add the control to be associated
2. Add a Label control
3. Set the access key
4. Associate the control to receive focus
Here's an example:
<asp:Label ID="lblLastName" runat="server"
AccessKey="L"
AssociatedControlID="txtLastName"
Text="<u>L</u>ast name: ">
</asp:Label>
<asp:TextBox ID="txtLastName" runat="server"></asp:TextBox>
Note that setting focus by using access key from a Label control requires that client scripting is enabled in the browser.
Tuesday, June 12, 2007
Cisco Switch - TFTP IOS Upgrade
Update, Copy, Backup, Restore IOS and startup-config are pretty much done in the same manner. First, you've got to configure the switch and the PC to talk then run the TFTP or FTP server and start the copy process.
Let's walk though how you can update Cisco IOS on a 6500.
Router> enable
Router# configure terminal
Router(config)# interface gig 9/1
Router(config-int)# switchport
Router(config-int)# switchport mode access
Router(config-int)# switchport access vlan 1
Router(config-int)# no shutdown
Router(config-int)# exit
At this point, we have turn port 9/1 into a layer 2 port on vlan 1. Now we need to assign an ip address to this default vlan so we can communicate to it.
Router(config)# interface vlan 1
Router(config-int)# ip address 10.10.10.1 255.255.255.0
Router(config-int)# no shutdown
Router(config-int)# exit
 The next thing we need to do is to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.
The next thing we need to do is to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.
Plug in the cable from the PC to the port we just configured; and to make sure the PC can talk to the 6500 we can try pinging it:
Router(config)# do ping 10.10.10.2
If you have a successful ping reply then you should be good to go. Launch the TFTP server and start the copy process. To copy from data from TFTP server to the switch use:
Router# copy tftp: disk0:
After you issue either of this command, you will be prompted for the FTFP server address and filename. Enter 10.10.10.2 and the filename you want to copy, then confirm it to start the copy process.
And to copy data from flash to FTFP server use the command:
Router# copy disk0: tftp:
If you are copying a rather large file then you should use FTP instead of TFTP and issue the command:
Router# copy FTP: Disk0:
I have run into some issue while moving a large file to the Cisco 6509. See this blog for more details.
Let's walk though how you can update Cisco IOS on a 6500.
Router> enable
Router# configure terminal
Router(config)# interface gig 9/1
Router(config-int)# switchport
Router(config-int)# switchport mode access
Router(config-int)# switchport access vlan 1
Router(config-int)# no shutdown
Router(config-int)# exit
At this point, we have turn port 9/1 into a layer 2 port on vlan 1. Now we need to assign an ip address to this default vlan so we can communicate to it.
Router(config)# interface vlan 1
Router(config-int)# ip address 10.10.10.1 255.255.255.0
Router(config-int)# no shutdown
Router(config-int)# exit
 The next thing we need to do is to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.
The next thing we need to do is to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.Plug in the cable from the PC to the port we just configured; and to make sure the PC can talk to the 6500 we can try pinging it:
Router(config)# do ping 10.10.10.2
If you have a successful ping reply then you should be good to go. Launch the TFTP server and start the copy process. To copy from data from TFTP server to the switch use:
Router# copy tftp: disk0:
After you issue either of this command, you will be prompted for the FTFP server address and filename. Enter 10.10.10.2 and the filename you want to copy, then confirm it to start the copy process.
And to copy data from flash to FTFP server use the command:
Router# copy disk0: tftp:
If you are copying a rather large file then you should use FTP instead of TFTP and issue the command:
Router# copy FTP: Disk0:
I have run into some issue while moving a large file to the Cisco 6509. See this blog for more details.
Monday, June 11, 2007
ProCurve Switch - TFTP Flash Update
To update the IOS on the HP's ProCurve switches you first need to configure an access port so it can communicate to the TFTP Server.
ProCurve Switch 3500yl-48G> enable
ProCurve Switch 3500yl-48G# configure terminal
ProCurve Switch 3500yl-48G(config)# vlan 1
ProCurve Switch 3500yl-48G(vlan-1)# ip address 10.10.10.1/24
ProCurve Switch 3500yl-48G(vlan-1)# exit
 Next, you will need to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.
Next, you will need to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.
Then the next step is to connect your machine to the switch; plug a cable from your laptop or PC to the switch. And just to make sure that the data can travel from one end to another, we'll go ahead and try to send a ping to the server:
ProCurve Switch 3500yl-48G# ping 10.10.10.2
If the ping is successful, you need to launch your TFTP Server, then you can go ahead and update the flash by issuing the copy command and pass to it the server address and the filename:
ProCurve Switch 3500yl-48G# copy tftp flash 10.10.10.2 k_12_02.swi
And if you need to update the secondary flash, then issue this command:
ProCurve Switch 3500yl-48G# copy tftp flash 10.10.10.2 k_12_02.swi secondary
I make a habit of using scripts to make the whole process easier to manage and make the update faster so here's the entire script:
enable
configure terminal
vlan 1
no ip add
ip address 10.10.10.1/24
exit
ping 10.10.10.2
copy tftp flash 10.10.10.2 k_12_02.swi
y
copy tftp flash 10.10.10.2 k_12_02.swi secondary
y
Note: If you use this script, make sure that you update the ip address and change the filename.
ProCurve Switch 3500yl-48G> enable
ProCurve Switch 3500yl-48G# configure terminal
ProCurve Switch 3500yl-48G(config)# vlan 1
ProCurve Switch 3500yl-48G(vlan-1)# ip address 10.10.10.1/24
ProCurve Switch 3500yl-48G(vlan-1)# exit
 Next, you will need to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.
Next, you will need to configure the network adapter on your PC or laptop and give it an address that's on the same network as the switch. In this case, I set it to be 10.10.10.2 255.255.255.0.Then the next step is to connect your machine to the switch; plug a cable from your laptop or PC to the switch. And just to make sure that the data can travel from one end to another, we'll go ahead and try to send a ping to the server:
ProCurve Switch 3500yl-48G# ping 10.10.10.2
If the ping is successful, you need to launch your TFTP Server, then you can go ahead and update the flash by issuing the copy command and pass to it the server address and the filename:
ProCurve Switch 3500yl-48G# copy tftp flash 10.10.10.2 k_12_02.swi
And if you need to update the secondary flash, then issue this command:
ProCurve Switch 3500yl-48G# copy tftp flash 10.10.10.2 k_12_02.swi secondary
I make a habit of using scripts to make the whole process easier to manage and make the update faster so here's the entire script:
enable
configure terminal
vlan 1
no ip add
ip address 10.10.10.1/24
exit
ping 10.10.10.2
copy tftp flash 10.10.10.2 k_12_02.swi
y
copy tftp flash 10.10.10.2 k_12_02.swi secondary
y
Note: If you use this script, make sure that you update the ip address and change the filename.
Friday, June 8, 2007
Cisco TFTP - Flash Update Problem
I was upgrading the IOS for the Cisco 6509s. I got Cisco TFTP Server setup and connected to it to download the file. The file was around 80Mb. TFTP Server threw an exception and shutdown. Upon restart, the file started to get downloaded but a few seconds later Cisco TFTP Server threw another error. This time I was able to view the error message and it said the transfer failed due to Synchronization Error.
I switched to SolarWinds TFTP Server and got a more detailed error saying the file was too large to be transferred through TFTP.
As an alternative, I used FTP Server from 3CDaemon and issued the command:
copy FTP: Disk0:
and it worked like a champ.
I had IIS running on my laptop so I turned off 3CDaemon and used IIS's FTP server. It worked out just fine.
So if you are transferring a large file you should use FTP and not TFTP to avoid potential problems and I also recommend 3CDaemon as it's got TFTP Server, FTP Server, Syslog as well as TFTP client all in one package.
I switched to SolarWinds TFTP Server and got a more detailed error saying the file was too large to be transferred through TFTP.
As an alternative, I used FTP Server from 3CDaemon and issued the command:
copy FTP: Disk0:
and it worked like a champ.
I had IIS running on my laptop so I turned off 3CDaemon and used IIS's FTP server. It worked out just fine.
So if you are transferring a large file you should use FTP and not TFTP to avoid potential problems and I also recommend 3CDaemon as it's got TFTP Server, FTP Server, Syslog as well as TFTP client all in one package.
File System Object
The FileSystemObject object library, which is part of the Microsoft Scripting Runtime library (Scrrun.dll) provides an object-oriented approach to directories & files manipulation. For instance, system folder creation and deletion is one common task your code will need to perform. Naturally, before you attempt to either create or delete a folder, your procedure will want to determine if it exists. The FileSystemObject library provides the perfect solution.
First, you'll need to set a project reference to the Scrrun.dll. The FileSystemObject is the top-level object within the file hierarchy, and you create an instance of it just like you would with any other object variable:
VB6
Set oFSO = New Scripting.FileSystemObject
ASP
Set oFSO = Server.CreateObject("Scripting.FileSystemObject")
The FolderExists() method returns True if the folder exists and False if not. The CreateFolder() and DeleteFolder() methods create and delete folders respectively. All three of these methods require the full path to the folder in question. The following code shows how to use these methods (assuming you've set a reference to the Microsoft Scripting Runtime library):
If Not oFSO.FolderExists("C:\Test") Then
Call oFSO.CreateFolder "C:\Test"
End If
Call oFSO.DeleteFolder "C:\Test"
Set oFSO = Nothing
First, you'll need to set a project reference to the Scrrun.dll. The FileSystemObject is the top-level object within the file hierarchy, and you create an instance of it just like you would with any other object variable:
VB6
Set oFSO = New Scripting.FileSystemObject
ASP
Set oFSO = Server.CreateObject("Scripting.FileSystemObject")
The FolderExists() method returns True if the folder exists and False if not. The CreateFolder() and DeleteFolder() methods create and delete folders respectively. All three of these methods require the full path to the folder in question. The following code shows how to use these methods (assuming you've set a reference to the Microsoft Scripting Runtime library):
If Not oFSO.FolderExists("C:\Test") Then
Call oFSO.CreateFolder "C:\Test"
End If
Call oFSO.DeleteFolder "C:\Test"
Set oFSO = Nothing
Wednesday, May 30, 2007
Basic SQL Syntax Troubleshooting
Developing dynamic web and/or desktop applications often involve querying the database for the desired data. One of the problems new programmers often run into is troubleshooting SQL syntax.
Here's a simple tip to help you troubleshoot your SQL syntax:
1. Write the SQL statement out to screen
2. Copy the SQL statement
3. Open the Access database
4. Create a new query
5. View the query text
6. Paste the SQL statement in the query window
7. Try to run the SQL statement
This should give you more info about the error you are running into.
But I am using SQL Server instead of Access database...
Don't worry, if you are running SQL Server or other databases, you can use Access and created linked tables to your database and take it from there.
Here's a simple tip to help you troubleshoot your SQL syntax:
1. Write the SQL statement out to screen
2. Copy the SQL statement
3. Open the Access database
4. Create a new query
5. View the query text
6. Paste the SQL statement in the query window
7. Try to run the SQL statement
This should give you more info about the error you are running into.
But I am using SQL Server instead of Access database...
Don't worry, if you are running SQL Server or other databases, you can use Access and created linked tables to your database and take it from there.
Friday, May 25, 2007
Optimize Your Website For Performance
Performance can affect the number of visitors come to your site. The faster the site load, the better experience the visitors will get and the chances of them coming back will also be higher.
Network latency, congestion, packet drops... are already reducing your application performance. If you, the developer, can do anything to speed up content delivery, by all means, you should do it.
Unfortunately, most developers often neglect to pay attention to this are since it's not something they can really visually see and fix because there is no error that will popup and say "Hey, I am slow... fix me..." or something like that.
Here are a few tips that any developer can use to help speed up their web pages:
If you get the opportunity, you should examine the HTML output for well known sites like Yahoo or Google and see how they optimize their site for performance. Chances are you will see these tips in action.
Network latency, congestion, packet drops... are already reducing your application performance. If you, the developer, can do anything to speed up content delivery, by all means, you should do it.
Unfortunately, most developers often neglect to pay attention to this are since it's not something they can really visually see and fix because there is no error that will popup and say "Hey, I am slow... fix me..." or something like that.
Here are a few tips that any developer can use to help speed up their web pages:
These tips will not significantly improve the performance of your web site as that will also depend upon how you compose your application but it will definitely improve the delivery of the page to the visitors. This is especially true if you have high traffic on your site.
Put CSS code at the top of the page: if you put CSS at the top of the page, the browser will read it first. When the browser renders a web page, it doesn't have to search up and down looking for the style rules.
Move JavaScript code down to the bottom of the page: JavaScript’s are mostly run on the client side AFTER the page has been rendered. Moving them to the bottom of the page will allow the browser to render other markup tags first and present the UI to the client faster.
Compress java scripts & remove white space: The browser doesn't care if you name your function with a single character nor does it care if the name is 50 characters as long as they are valid. White spaces might make your code look good but will not help when it comes to speed. The less data your server has to spit out the faster your page will be delivered over the wire.
Remove duplicate and/or unused scripts: If it's not being used, remove it. If anything, it will cause more load on your network and create more confusion having it there when it comes time to troubleshoot some problems.
Do not mix Javascripts and HTML markups: Sometimes, you will need to use Javascripts to produce HTML markups. But try to reduce this to a minimum and let the browser finish one thing before it starts the next one (ie: complete HTML render before executing javascript...)
Move CSS & Javascripts out of HTML markups: Don't make the browser go back and forth between HTML markups and javascripts when it renders the page as there is a performance cost to this.
Add expires header: The browser save the pages onto the hard disk so that it can load the same site faster next time around. If there isn't a need for this, add expires header to it doesn't write the pages to disk.
Disable viewstates: ASP.net pages have viewstate enabled by default which adds a bunch of encrypted code to the page. If viewstate is not required, disable it and it will improve the page performance.
If you get the opportunity, you should examine the HTML output for well known sites like Yahoo or Google and see how they optimize their site for performance. Chances are you will see these tips in action.
Thursday, May 24, 2007
Ping Flood Attack
A ping flood is a simple Denial of Service (DoS) attack where the attacker sends a massive number of ICMP Echo Request (ping) packets to the victim in hope of overwhelming the victim and consuming both outgoing and incoming bandwidth on the victim's network. An effective attack could render the victim's network useless.
This type of attack only succeeds if the attacker has more available bandwidth than the victim (like a T3 versus and DSL line) which is very unlikely. To get around this, the attacker normally use an army of computers (a network of computers that attacker has control called zombies or bots) numbered in the hundreds or thousands to attack the victim with their combined bandwidth power.
Defense Your Network
To reduce the effects of ping flood attack, one can use a firewall to inspect the traffic and filter ICMP Echo Request packets. However, doing this can also have its side effects such that it prevents legistimate users from pinging their hosts. For this reason, we can use firewall to authorize ICMP Echo Request packets from legistimate source only.
This type of attack only succeeds if the attacker has more available bandwidth than the victim (like a T3 versus and DSL line) which is very unlikely. To get around this, the attacker normally use an army of computers (a network of computers that attacker has control called zombies or bots) numbered in the hundreds or thousands to attack the victim with their combined bandwidth power.
Defense Your Network
To reduce the effects of ping flood attack, one can use a firewall to inspect the traffic and filter ICMP Echo Request packets. However, doing this can also have its side effects such that it prevents legistimate users from pinging their hosts. For this reason, we can use firewall to authorize ICMP Echo Request packets from legistimate source only.
Sunday, May 20, 2007
Access IIS application from computers on the same network
A user was having problem accessing his website on the network. The site is working fine from the local machine. However, when he tries to access the same site from a computer on the network, it's not working.
The problem and attempted answers can be viewed in this post. You should read the posts in that forum before continuing on this blog so things would make sense when you read the paragraphs below.
Let's logically work through the posts and try to sort out the problems:
1. Setting up a new website, IP address and port number is not necessary as the original site already working on the machine IIS is running from. Since all the computers are on the same network, you should be able to access it by computer name as well.
2. On Win XP, you can actually host more than one sites and running more than one IP on the same computer. But this won't be discussed in this blog. On top of that, it's not even relevant to the problem we are trying to solve.
3. This shouldn't be security issue also since IIS applications typically run on anonymous account by default and permission is granted when the site is set up; unless you specifically make change to it.
The true answer to this lies in Windows XP Pro SP2's built-in Firewall. Open port 80 in Windows Firewall to allow web traffic should solve this issue. If there are other software firewall running, check and open port 80 as well.
Brian Dao
The problem and attempted answers can be viewed in this post. You should read the posts in that forum before continuing on this blog so things would make sense when you read the paragraphs below.
Let's logically work through the posts and try to sort out the problems:
1. Setting up a new website, IP address and port number is not necessary as the original site already working on the machine IIS is running from. Since all the computers are on the same network, you should be able to access it by computer name as well.
2. On Win XP, you can actually host more than one sites and running more than one IP on the same computer. But this won't be discussed in this blog. On top of that, it's not even relevant to the problem we are trying to solve.
3. This shouldn't be security issue also since IIS applications typically run on anonymous account by default and permission is granted when the site is set up; unless you specifically make change to it.
The true answer to this lies in Windows XP Pro SP2's built-in Firewall. Open port 80 in Windows Firewall to allow web traffic should solve this issue. If there are other software firewall running, check and open port 80 as well.
Brian Dao
Subscribe to:
Posts (Atom)
